Based On a True Story
Table of contents
Law and Order and Chill
We don't have great Internet at our house out in the sticks. Okay, we really don't have any Internet outside of cellular hotspots with limited data and one bar of service. These ballyhooed, newfangled streaming services are just not in the cards. Thus, satellite television is the order of the day. And Law and Order (and its many spinoffs) are just kind of...there. Background filler, white noise, the adequate accompaniment to a standard week night.
And like most Hollywood fare, let's just say that I'm tickled at times at their portrayal of technology...especially computers and networking.
IP Address Tracker 1.0.5
One technical concept that TV shows have had a particularly hard time with is the IP Address. An IP Address (short for Internet Protocol Address) is your "mailing address" on the Internet. It tells other computers how to find you. If you're reading this right now, chances are you have an IP address. You can even figure out what it is! Just use your favorite search engine and type "What's my IP?". Here's an example from Show my IP.
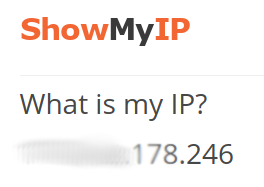
There are elements to a postal address that you have to follow if you want your package successfully delivered. A zip code has five digits, for example. You need to include the city, the state, and the street address. An IP Address is similar: it has a format. There are rules. There are parts of the address that specify the network you are on (kind of like a zip code) and parts that specify your individual computer. Specialized computers known as routers use this information to "deliver" your data to an Internet destination.
I'm a super networking geek: I went to a Cisco Networking Academy in high school and worked as a network engineer for 15 years. IP addresses are my jam. So, I obviously couldn't help but pause my DVR and take a poor cell phone screen shot when I saw this...
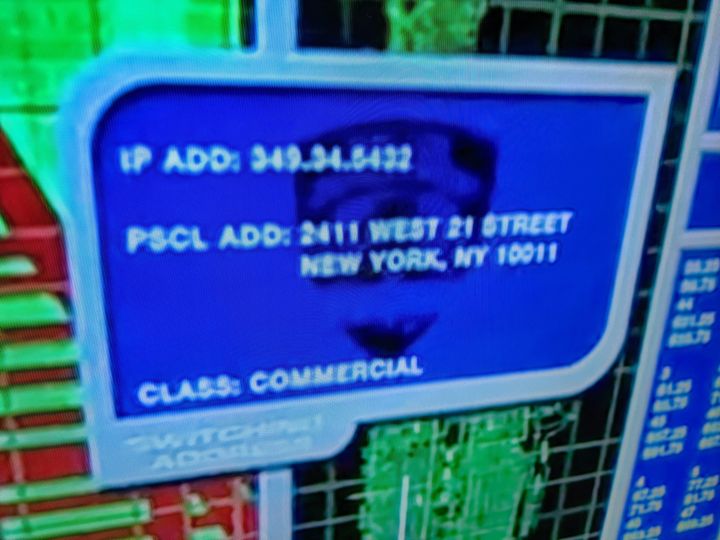
Note the "IP ADD" field with the value 349.34.5432. There's something very wrong with this, and to avoid spoilers you can find the answer in the footnotes1.
But don't worry, it's not like they would make this mistake more than once.
Oh, wait...
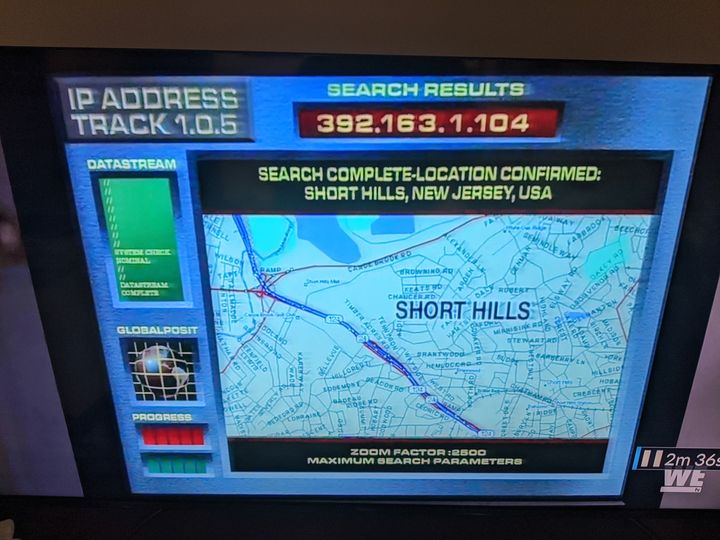
Once again, I'll direct the interested reader to the footnotes2.
For good measure, I present the WIFI Tracker 2.11. Including features such as Acquire, Locate, and Localize?
![]()
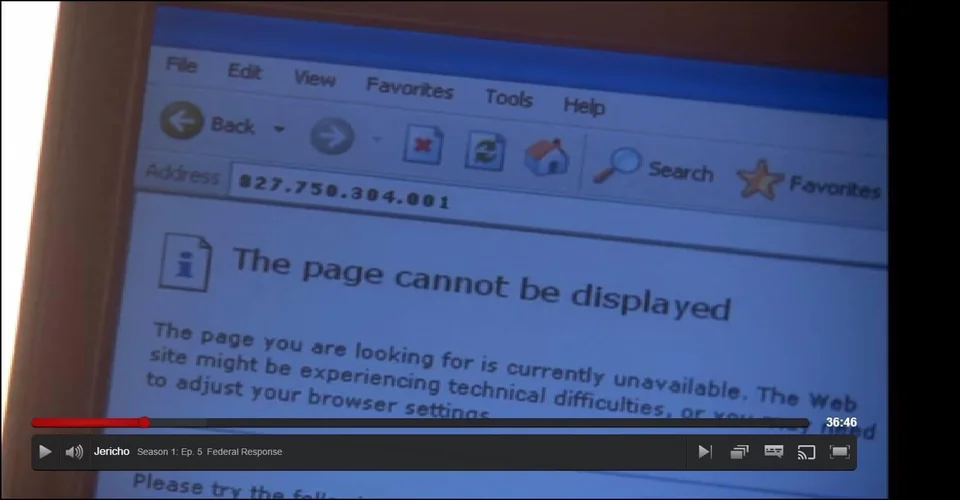
In fairness, the Law and Order franchise isn't the only TV series to make these mistakes. Here's an image from the short-lived TV series Jericho, courtesy of Reddit. What's wrong here? The answer is in the letterbox3.
So needless to say, I've developed a tendency to fact check portrayals of computer technology on popular TV serials.
Lava Lamps and...Encryption?
I've been picking on Law and Order and, to a lesser extent Jericho. But as it happens, the TV show that provides the inspiration for this discussion is NCIS. Like Law and Order, it has approximately eleventy-billion episodes and thus is sometimes just there in the background.
And one lazy Saturday morning while NCIS is "just there", I see a wall of lava lamps on the television screen, and hear the following dialog exchange:

So what was Rafi's job?
You're looking at it. He was a janitor. He kept our encryption engine clean.
What, you use lava lamps as an encryption engine? No AES or key block ciphers?
They're our secret recipe.
Fuming, I immediately transform into self-righteous know-it-all engineer mode. BS I exclaim! Lava lamps for encryption? That is absolutely absurd!
And then I Googled it and realized, well I was only half right. Lava lamps can be useful for encryption, just not quite in the way NCIS portrayed.
Cloudflare and the Search for Entropy
As it turns out, NCIS was borrowing a story from the Internet. CloudFlare has a wall of lava lamps in their San Francisco office.

These lava lamps feed into Cloudflare's cryptographic processes, but it falls a bit short of the encryption engine as portrayed on NCIS. To understand why, let's look at an encryption engine, i.e. one of those "key block ciphers" discussed in the NCIS episode.
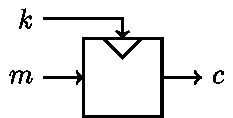
A block cipher takes three inputs. The message m (or plaintext) is the message that you want to encrypt. The key k is chosen at random, and is combined with m to create the ciphertext c, which is the encrypted message. Block ciphers follow Kerckhoff's principle which states that only the key needs to remain secret. As long as we pick a secure block cipher such as AES, keep our key secret, and choose our key at random, it should be infeasible4 to recover the original message from the ciphertext.
Blockciphers are super cool, and their inner workings are bit beyond the scope of this article, but suffice to say that when combined with a secure mode of operation they form a solid basis for an encryption engine.
Alas, as it turns out lava lamps make poor encryption engines. Try as I might, I can't find a way to stuff either a message or a key into a lava lamp. The only input is a 115V electric cord, and the only output is heat and bright, colorful patterns. Excessive force would only result in broken glass, cut fingers and first-degree burns.
Thinking back to our block cipher, the key part (pun intended) is that the key must be chosen at random and must remain secret. An adversary who can recover the key can recover the original message. So how can we prevent the attacker from recovering the key?
- We protect the key - limiting access and hopefully preventing it from being compromised directly
- We choose a really long key. AES keys are either 128, 192, or 256-bits long.
- We choose our key at random, ensuring there are no patterns.
If the adversary can't recover the key directly, then the best attack against a secure encryption scheme is brute-force (i.e. try every possible key). And with a really large key we're back to that whole infeasible4 quality we want with our encryption engine.
But we're still stuck at that picking the key at random part. How the heck do we do that?
Random Number Generation is too Important to be Left to Chance5
Block ciphers are but one tool in a cryptographer's chest. Another very useful tool is the Pseudo-Random Number Generator (PRNG). Specifically, a subset of a PRNG known as a Cryptographically Secure Pseudo-Random Number Generator (CSPRNG).
A CSPRNG has a very interesting property: feed it a number as an initial "seed" and it will generate numbers that are indistinguishable from randomly generated numbers. We can use this CSPRNG to generate keys for our block ciphers or other cryptographic processes. The only catch is that it is deterministic. If you feed the CSPRNG the same seed value, it will produce the exact same sequence of "random" numbers. If our adversary can guess the initial seed, they can reproduce the "random" output.
Thus, we're back to a chicken and the egg dilemma: a CSPRNG can generate "random" values but only if we provide it with a truly random seed. So how can we get that initial random value?
The answer is entropy. As it turns out, lava lamps are a fantastic generator of entropy, i.e. randomness. And it is this property that makes them useful to CloudFlare's cryptographic processes.
Mix and Match
We've established that for many cryptographic processes, such as generating keys, or seeding a CSPRNG, a random number is required. So instead of leaving it up to individual applications to solve this problem on their own, operating systems such as Windows and Linux provide their own CSPRNG. Linux provides access to its CSPRNG via /dev/random and /dev/urandom. The Linux CSPRNG is complicated6 and analysis is beyond the scope of this article.
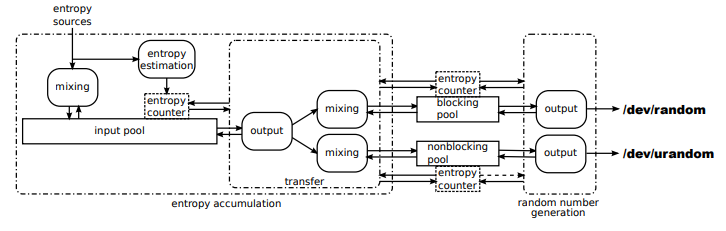
The Linux CSPRNG is designed to take in entropy from multiple different sources, such as keyboard strokes, mouse movement, and hard drive noise. It can even take input from dedicated hardware sources, such as the RDRAND instruction in modern CPUs. These different sources are mixed together, using a mixing function, adding to the overall entropy pool that ultimately feeds the output of the Linux CSPRNG.
The really cool part about the mixing process is that if there are multiple inputs to the process, as long as the attacker cannot recover all of the inputs, the attacker is unable to infer the final result.
This is why CloudFlare utilizes Lava Lamps. By having a wall of Lava Lamps and taking pictures at regular intervals, CloudFlare is able to feed the entropy created by the Lava Lamps into the Linux CSPRNG. This helps ensure that if the other inputs to the Linux CSPRNG are ever compromised, that CloudFlare can still trust the Linux CSPRNG and thus generate cryptographically secure key material.
For further information, I highly recommend reading CloudFlare's blog posts on this topic. The non-technical version is here, the nitty gritty details are here, and it appears they even had fun with the NCIS portrayal and purchased the assets (or at least the domain) of their competitor.
Stay Tuned
It turns out this concept of mixing two or more sources together has another important use; it's the basis of hybrid encryption in TLS. This gives us the best of both worlds: protection against a potential future post-quantum adversary while ensuring our data stays protected in case said post-quantum encryption scheme winds up broken on a laptop over a weekend.
-
There's a few things wrong here. First, it isn't following Dot-decimal notation correctly. There should be four octets like 192.168.0.1. Secondly, each number in dot-decimal is an octet which consists of eight bits. Thus, the valid numbers are between 0 and 255. Both 349 and 5432 are right out. ↩
-
This time they got Dot-decimal correct, but 392 is still greater than 255. As an aside, I'd pay good money for a traceroute tool with this level of accuracy... ↩
-
Our IP address here is 827.750.304.001. The first three numbers still break the whole greater than 255 rule. The last number is technically okay with the leading zeroes, but most implementations will strip those. As for the reference, What burns with the light of a thousand suns and is in the letterbox? ↩
-
Given enough time, every cryptographic scheme minus the One-time pad can be broken, theoretically. Thus, we rely on the term infeasible. If using AES with a 128-bit key, it would take 1 billion years to crack relying on brute force alone. ↩↩
-
Attributed to Robert Coveyou who was apparently a bad ass, an expert in PRNGs, worked on the Manhattan Project and was active in the Civil Rights movement. ↩
-
Seriously, it's complicated ↩